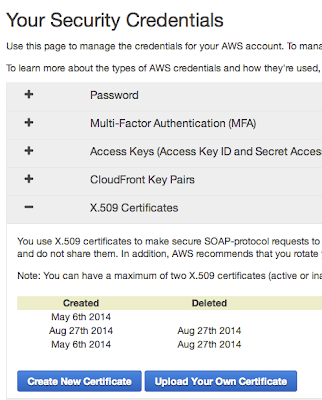
You will need X.509 certificates when you send a SOAP request to AWS or use command line tool.
There are two ways to create X.509 certificates.
(1) If you are not using IAM account:
You can create certificate on AWS console.
Each account only have a maximum of two certificates at a time.
(2) If you are using IAM account:
You need to create certificate by yourself.
1. Create private key
You need to create a private key first before create a certificate,
because you will use this private key to create a certificate.
2. Create certificate
Once you finished the step one, you can use the private key to create a certificate.
3. Copy the content of certificate
After you finished all the steps, just copy the content of the certificate.
4. Upload the content of certificate
Go to the IAM management console.
1. Select an IAM user
2. Click "User Actions"
3, Click "Manage Signing Certificates"
4. Click "Upload Signing Certificates"
5. Paste the content
6. Click "Upload Signing Certificates"
Done. Now you can send a SOAP request to AWS or use the command line tools.
There are two ways to create X.509 certificates.
(1) If you are not using IAM account:
You can create certificate on AWS console.
Each account only have a maximum of two certificates at a time.
(2) If you are using IAM account:
You need to create certificate by yourself.
1. Create private key
You need to create a private key first before create a certificate,
because you will use this private key to create a certificate.
openssl genrsa 2048 > private-key.pem
2. Create certificate
Once you finished the step one, you can use the private key to create a certificate.
openssl req -new -x509 -nodes -sha1 -days 99999 -key private-key.pem -outform PEM > cert.pem
3. Copy the content of certificate
After you finished all the steps, just copy the content of the certificate.
ken@build:~$ cat cert.pem
-----BEGIN CERTIFICATE-----
MIIDXzCCAkegAwIBAgIJAJxcjyc5F908MA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX
aWRnaXRzIFB0eSBMdGQwIBcNMTQwODI3MDc1NDAyWhgPMjI4ODA2MTAwNzU0MDJa
MEUxCzAJBgNVBAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJ
bnRlcm5ldCBXaWRnaXRzIFB0eSBMdGQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAw
ggEKAoIBAQCk8L/z2O84OcRno7YgGu0UkjnABuXhIM96RfZZKhqg74hga7nsLPLK
CzhtslDKAOEjxASo7L0Iq6/5kxJZp4cZakKacDOvnnv2HwQxCXGUEadXcmeknfAh
SvyRYS3FrKj4/oth+pwUm6nvd9fGYg01rJITUQupeADCqhSJUypZbQUypmPxf8Sg
ek7ZW5ErPuyZZ+WmL6TzZaQXfZqvPrN25hRg7AboB8SIKgusUrLK6WgnISlJ7fDh
kCpsy8qSD+Lu74h2hW6TiLy2qJbcTKn8sKb1C4XgWb1FBMzqfJQWtCMVWtDoyzZH
Vj07gzeTDkQ1EvUKHk26x6MEsOlcTV9XAgMBAAGjUDBOMB0GA1UdDgQWBBQOYnDF
FYz2o3+AlVHWwPIzlcFs4DAfBgNVHSMEGDAWgBQOYnDFFYz2o3+AlVHWwPIzlcFs
4DAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBBQUAA4IBAQBPE3ikbJ/vH6QfkwUK
qot+nU15keDSZ2c6itRnNuwjfF8lsZQCJ66w2H+HXCLBjnPymemcTPTMUqfovpFs
oNohRuQS6IoIrvgXAbb2X4BhygPDNSQPktGVo8qjKUyxYZa4Su8NFkb+OzZWDR4K
KN+OLFfaT6cx8o9o5M7cmNRokFisWynJ33EoKj1lW5YIwTwb1VKz4hXW+gKZFX7u
pgE1yzkOcoUW5EykNsGUaqLSdycxmDO866IFn6px9etxpIkQwUi+rb78tX6pNtpa
IBTsfPBqovXRdMe6mq5uO8x4Nrb47w8DZkrQSTMt1ll4t0bUL15o/6cQ5ajGaaGA
QVtO
-----END CERTIFICATE-----
4. Upload the content of certificate
Go to the IAM management console.
1. Select an IAM user
2. Click "User Actions"
3, Click "Manage Signing Certificates"
4. Click "Upload Signing Certificates"
5. Paste the content
6. Click "Upload Signing Certificates"
Done. Now you can send a SOAP request to AWS or use the command line tools.
.png)